Back to Journals » Psychology Research and Behavior Management » Volume 15
A Preliminary Validation of the Chinese Version of the Information Technology Identity Scale
Authors Wang P , Liu H , Wang X, Yuan X , Sun Y, Xiao L, Li W , Ma C
Received 9 December 2021
Accepted for publication 18 February 2022
Published 25 March 2022 Volume 2022:15 Pages 751—762
DOI https://doi.org/10.2147/PRBM.S352365
Checked for plagiarism Yes
Review by Single anonymous peer review
Peer reviewer comments 2
Editor who approved publication: Dr Igor Elman
Peng Wang, Haotian Liu, Xiao Wang, Xiqing Yuan, Yu Sun, Li Xiao, Wenxuan Li, Chong Ma
Faculty of Education, Department of Psychology, Shandong Normal University, Jinan, People’s Republic of China
Correspondence: Li Xiao, Faculty of Education, Shandong Normal University, Jinan, People’s Republic of China, Tel +86-17806815755, Email [email protected]
Background: Information technology has become an irreplaceable part of people’s lives, and the interaction between information technology and self-identity has produced a new type of information technology (IT) identity. However, there is no measurement tool for this concept in China. The main aim of the study was to revise Carter’s IT Identity Scale in the context of Chinese cultural background and to determine whether the Chinese version is congruent with the English version.
Methods: In this study, we revised the scale on the basis of the information technology identity scale developed by Carter, translated the scale according to the Chinese cultural environment. Our sample size was 408, and all of them were junior middle school students. After testing this sample, we carried out item analysis, validity analysis, and reliability analysis.
Results: (1) The correlation coefficients between each item and the total score were significant (0.775– 0.885). (2) The three-factor structure (relatedness, dependence, emotional energy) of the Chinese version of the IT identity scale was consistent with the original scale. The values of the factor loadings of each item in the three factors of confirmatory factor analysis (CFA) were all greater than 0.700, and the model fit indexes (CFI, NFI, NNFI, TLI and IFI) were all greater than 0.900, indicating a good model fit. (3) Average variance extraction (AVE), composite reliability (CR), Pearson correlation, and the square root of AVE indicated good convergence and discriminant validity. (4) The ɑ coefficients and CR of the three dimensions (ie, relatedness, dependence, emotional energy) were all greater than 0.800, and the split coefficients were all greater than 0.800, indicating high reliability.
Conclusion: The Chinese version of the information technology identity scale presented satisfactory psychometric properties and shared many similarities with the original version. Ultimately, we revised an information technology identity scale suitable for Chinese culture.
Keywords: information technology identity, self-identity, information technology, scale revision
Introduction
Information technology has become an irreplaceable part of people’s lives.1,2 This term refers to the various technologies that are used to manage and process information, including sensing technology, computer technology, and communication technology3 (eg, smartphones, MS Office, and WPS Office). The use of information technology has made a significant impact on all aspects of life, not only at material level but also on a spiritual level.4 It has long been reported that young people’s experiences are shaped by the interactions that they maintain within multiple social worlds.5 During this process, the self-identity of users and information technology interact with one another and result in a novel form of information technology identity (referred to as IT identity).6
Carter defined IT identity as a new type of identity, ie, the extent to which a person’s interactions with an IT are viewed as integral to his or her sense of self.1 This form of identity grows from interactions between individuals and information technology during which the use of information technology gives individuals many abilities that they did not have in the past, such as high efficiency, connectivity, and autonomy, that enable them to expand their self-understanding and construct a new identity. When separated from the interaction between individuals and information, as well as losing the capabilities of IT, individuals will experience self-shrinking. That is, due to the lack of information technology resources, individuals’ self-consciousness will shrink. For example, the separation from IT limits the channels for individuals to communicate with others, partially blocks individuals from maintaining social relations, and affects individual self-consciousness in social interaction, which further affects individuals’ IT identity.6
Literature Review
Identity
Psychologists and sociologists have carried out research on “identity” and constructed a variety of theories. These theories can be divided into Role Identity Theory,7,58 Personal Identity Theory,8 and Social Identity Theory,9 all of which emphasize the interaction between society and the self. As an intermediary between people’s behavior and social structures, individual identity is affected by social structure at the same time. It is also shaped people’s attitudes and behaviors.
Thoits & Virshup identified clear boundaries between personal identity, role identity and social identity.10 They argued that generalized social identity works at both the individual and collective levels. On the individual level, identity functions as the self-identity of the individual, which is a variation of the social category used to describe “I am.” This categorization includes role identity, as it is described by McCall & Simmons and Stryker.11,12 At the collective level, identity is reflective of the overall group, which is a variation of the social category that describes “Who.” This categorization includes the narrow social identity proposed by Tajfel and Turner.13,14 Characteristics of both personal identity and social identity are simultaneously reflected in the self, but they have their differences. Personal identity is defined by characteristics unique to the individual, while social identity reflects the identity of self-social groups or categories and is the construction of social relationships in self and vast group categories. The difference between them is to be paid in self.15
The theoretical basis of identity is rooted in Mead’s symbolic interactionism and Burke’s identity control theory (ICT).12 The theory of symbolic interaction focuses on instances of indirect communication in which individuals communicate through “symbols”. The concept of the self is a combination of “I” and “Me.” “Me” refers to the self in the society formed through role play, and “I” refers to the independent individual who is not the object of consciousness. Mead believes that “self” originates from social interaction and that symbols play an important role in its development. ICT,12 affect control theory,16 and self-verification theory17 all conceptualize identity processes as control systems that regulate the perception of self-relevant meanings of actors.
The Relationship Between Identity and Information Technology
MeyRowitz was the first researcher to explore the relationship between information technology and identity. He noted that electronic media (eg, Twitter) have restructured patterns of social interaction, and that new technologies weaken and break down physical and social distances. According to MeyRowitz, in the constant renewal of new technologies, individuals will redefine the framework in which the self acquires cues, so as to influencing identity.18
Altheide further explained that information technology brings novel forms of interaction (eg, new options, organizations, and information presentation models) and creates new environments for self and recognition development.19 The keyboard opened new pathways of interaction and offered novel opportunities for collective dependence and flow.19 Carter asserted that IT is a unit of technology (ie, a hardware device, a software application, or a software application environment) that an individual consciously engages with, which is a concept that has implications about what types of IT are most likely to foster a strong IT identity.20
Currently, scholars use the concept of information technology identity to explain the identity generated by using information technology such as smart devices, social networking sites and social media, resulting in concepts such as social networking site identity and social media identity, but which are essentially information technology identities. A study showed that employees’ corporate social media identities can foster support among colleagues, which in turn has a positive impact on job performance and job satisfaction.21 A study on the reliability of patients reporting their health found that patients were asked to measure and report their health using health care services provided by smartphones in the absence of doctors and nurses, and that perceived mobile technology identity directly affected the reliability of self-reporting.22 Esmaeilzadeh’s research found that the identity verification process (IT characterizes through IT experience) fosters IT identity, which, in turn, encourages individuals to engage in beneficial post-adoption behaviors such as feature use and enhanced use.23 Tseng found in virtual retail environments, the characteristics of augmented-reality interactive technology—ownership control and rehears ability—may engender self-referencing, which further fosters information technological identity, then results in brand love.24 This shows that in the mobile information era, scholars are concerned with the application of IT identity theory in mobile IT usage research.
Role Identity
Role identity includes all of its internal changes and diversity, involving self and definition and division of others, inclusions and overall, is a recognition of a role of one thing in other things.7,58
Burke and Stets said role identity (eg, work role, parenting role, etc.) refers to internalized expectations about what it means to be competent while performing a certain role.25 Riley and Burke emphasized that the self-concept generated by role identity reflects that individuals obtain relevant information from others. They also asserted that role identity is a process of self-regulation in which individuals obtain meaning from self-attempts and role verification.26
Building on this perspective, Chen and Wang extend the concept role identity to user behavior in virtual communities, which is reflected in the user’s understanding of their own position and triggers role-playing behavior.27 The development of role identity and the stimulation of community attributes may trigger role conversion.28
In the context of people’s work lives, the use of information technology has an impact on individual work content and work efficiency. When people change their perception of the original work, that is the cognition of the original role. Information technology thus has an impact on role identity. Burke and Stets asserted that role identities are verified when individuals perform in ways that confirm their internalized expectations about what it means to be competent in a certain role.29 In other words, if people associate information technology with their own work roles, they use it to enhance recognition and maintain a sense of role identity. This maintenance thus ultimately enhances an individual’s acceptance of a certain type of technology. For instance, Kim et al found that online self-presentation motivated people to purchase avatars and decorative items on virtual community websites.8 In summary, people use information technology to buy things that match their roles as a means of reflecting their unique self-image and self-identity.
The COVID-19 outbreak has had a huge impact on various industries. Teachers are teaching online through Internet platforms. As offline teaching is replaced by online teaching, teachers need to acquire a lot of information technology skills to adapt to online teaching. In the process of teaching and lesson preparation, teachers’ role identity has also changed.30,31
Personal Identity
In the context of social media, the anonymity of online social communication gives people more freedom to express their true feelings, expand their social networks, and strengthen their ties with others,32 which helps shape self-image and, in turn, strengthens the impact that information technology has on personal identity.24 The internet provides individuals with deficits in self-concept with a tempting environment to socially interact with others anonymously and to obtain success through Internet gaming or other such activities.33
According to Kokswijk, “for some adolescents, their virtual personas are at least as important as their real life image”.34 Valkenberg and Peter believe that adolescents are more willing to disclose their so-called true selves on the internet because the anonymous environment reduces social expectations and the risks of social sanction that exist in face‑to‑face interactions.35 Specifically, Valkenburg has said that cyberspace offers every individual an opportunity to instantly change their assumed identity and that avatars can provide adolescents with fun and safe ways to explore different personalities and express themselves while keeping their real identities secret.36 The anonymity of avatars can also give adolescents the courage to act out their fantasies in ways that they normally would not.9
Social Identity
Tajfel explained that the formation of social identity occurs when “An individual individual recognizes that he (or she) belongs to a specific social group, and at the same time recognizes the emotional and value meaning brought to him (or her) by being a member of the group”.37
Shotter once said that “The consciousness of the inner life is created through the linguistic communication that takes place in social life and discourse practice”.38 Other researchers working on related topics have found that individuals can improve their self-worth and self-esteem through social identity. Creating a social identity also strengthens the group as a whole by promoting group belonging, which often involves excluding other groups.39
In the context of the online communities, common topics and points of interest enhance social interaction, deepen emotional connections, and make people feel a strong sense of social identity within a given online space.40 Information technology thus has an impact on social identity. When people put emotion into their engagement with virtual network societies and create social identity, this identity also strengthens their investment in and use of the community.41
The relation between social identity, self-identity, and information technology is exemplified in a Chinese social networking service, ie, douban.com, which allows users to cultivate their interest and customize the features that work best for them.42 Personal interests are at the center of Douban user’s self-narrative and serve as the starting point for people to construct their self-identity.43 A user’s perception of their similarity to others who come from the same background (ie, us) and their perception of the differences that exist between them and other group members (ie, them) function as the conditions for constructing social identity.37 The social identity of Douban’s users is also created through the process of perceiving internal identity and external difference.44 Douban users can also “make like-minded Douban friends” based on their shared interests, which further kindles a sense of internal life and promotes self-narrative through user interactions.42 Interpersonal interaction allows individuals to “find more things that they might like and find more interest in”, which affects identity construction by expanding the field of self-narrative.45
The Expansion of Self-Identity by Information Technology
When individuals identify with a certain type of information technology, they demonstrate three types of perception: relatedness, dependence, and emotional energy.1
Relatedness refers to the degree to which the boundary between self and information technology becomes blurred and the individual develops a sense of connection to information technology. For example, a user might not be able to make a clear distinction between their own abilities and the abilities granted by information technology.1
Dependence refers to the degree of individual dependence on information technology. The more widely used a certain type of information technology is, the more people rely on it to achieve their goals. McMillan and Morrison have said that people are becoming increasingly dependent on the internet to sustain their relationships with family and friends and engage in work and play.24 Ling and Yttri have also commented that because new forms of communication allow for greater flexibility in coordination, people are becoming more reliant on them to meet social expectations.45
Emotional Energy refers to ongoing positive emotions that are associated with information technology, such as emotional attachment and enthusiasm. When people receive positive feedback while interacting with a certain information technology, they often experience positive emotions, such as confidence and trust, that encourage them to continue using the technology.4
Carter developed an IT identity scale containing the three factors of relatedness, dependence and emotional energy, and he examined how well the scale performed on the three factors. This process involved performing a factor analysis (principal axis factoring) with oblique rotation (ie, direct oblimin).46 Information technologies (eg, the internet, smartphones, and software) in China are developing rapidly, and their use is becoming commonplace. Researchers, government authorities, and parents are mostly concerned with the negative effects of information technology (shyness,47,48 loneliness,47,48 internet addiction,49 and depression50) and have neglected to examine its potential benefits, which has led to a relatively incomplete understanding of IT. Because of this, a measurement tool is urgently needed to assess the current status of information technology identity in China. For this reason, we revised Carter’s information technology identity scale with the aim of creating an instrument that can reliably and validly assess the identity of information technology within China’s cultural context.
Methods
Participants
Taking a class as a unit, we randomly selected 408 students (Mage=13.48, SD=0.914) from the eighth grade in the second affiliated middle school of Shandong normal University and Qilu Experimental School, five classes in total, as subjects to test the scale.The test is led by graduate students in psychology and all data completed in one collection. There was a moderate ratio between boys and girls, and their guardians signed a form that consented to their participation in the study.
Instrument
Information technology identity scale includes three factors: relatedness, dependence, and emotional energy.5 In the initial inventory, these three factors each included four items. After adjustment, each factor contained three items, for a total of nine items. Each item in the scale is scored on a five-point scale: strongly disagree, disagree, unsure, agree, and strongly agree. All items were positive and scored on a scale of 1 to 5 respectively.
Carter measured IT identity by analyzing user experiences of MS Excel, a pervasive and well-established technology with a relatively unchanging feature set.5 He found evidence that IT identity can be measured using three factors that reflect the strength of positive self-identification with IT. The purpose of the current study was to test the applicability of this scale in the Chinese context. We maintained a three-factor structure for the scale but attributed three items to each of the factors instead of four.
Procedure of the Study
Shuttleworth and Cowief have explained that back translation is a process in which a text that has been translated into a given language is retranslated into a Second Language.51 The process is as follows: First, we invited psychology professors and graduate students to translate the IT Identity Scale developed by Carter, and after discussing it, a consensus was reached on the presentation of the items. Next, we sought out individuals who were proficient in English but not psychology to translate the Chinese scale into English and then discuss with them about the inconsistencies that existed between the original and translated versions. Additional language adjustments have been made to achieve the aim of ensuring that the English is consistent with the original version, and the final Chinese items have been formed by this approach.
In China, many individuals and groups, especially enterprises and schools, use WPS Office for office work because WPS Office Personal Edition and Enterprise Edition can meet the different office requirements of individuals and enterprises.44 We replaced the MS Excel usage scenario with the WPS Office usage scenario. We made this shift because WPS Office better fits the context of Chinese work scenarios, and its functional design aligns with the thought processes of Chinese people.52 Although WPS Office’s current domestic market share is less than MS Office’s, its number of monthly active users increased by 8.8% within the first quarter of 2020.45 WPS Office has strong development prospects,53 so we decided to adopt its use situation as a substitute in the scale.
Because there are three groups of questions in the original scale that hold similar meanings in the Chinese context, we integrated each group of questions into one item:
Q3: When thinking about myself in relation to my WPS Office, I feel energized./When thinking about myself in relation to my WPS Office, I feel pumped up.
Q6: When thinking about myself in relation to my WPS Office, I feel connected with WPS Office./When thinking about myself in relation to WPS Office, I feel linked with it.
Q9: When thinking about myself in relation to WPS Office, I a feel dependent./When thinking about myself in relation to WPS Office, I feel reliant.
According to existing research, the three-factor structure of Carter’s IT identity scale is universal.1,2,5,38 The purpose of this study is to verify the factor structure of the scale in the context of Chinese culture, assuming that there is a similar three-factor structure in our samples, so directly through confirmatory factor analysis, just like Bai et al.54–56
After the test, we sorted out the results and imported the structured data into IBM SPSS Statistics 26.0 and Mplus 8.3 for analysis, and the code we used was in the Appendix. We then analyzed the items according to the order. The purpose of the confirmatory factor analysis and the calculation of α coefficient was to check the reliability and validity of the scale according to the discrimination of the items of the scale according to the results. We checked whether the relationship between each item and the corresponding factor aligned with the theoretical relationship that existed between them in the original scale. Each item of the scale conformed to the language expression of Chinese cultural characteristics but did not change the structure of the original scale, which allowed us to determine the structure and items of the Chinese version of the scale based on the test results.
Results
Item Analysis
Analysis of the Discrimination of High and Low Groups
The results of the sample were divided into high and low groups according to the first 27% and the last 27%, and then item discrimination analysis was conducted. As Table 1 shows, there were significant differences between the high and low groups of all the items. A total of nine items were considered to be discriminative and were thus retained.
 |
Table 1 Item Discrimination Analysis |
Confirmatory Factor Analysis
As illustrated in Figure 1, confirmatory factor analysis (CFA) was carried out for a total of three factors and nine items. The sample size of this analysis was 408, which was more than 10 times the number of analysis items. The standardized factor loadings, which are depicted in Figure 1, exceeded 0.7 and ranged from 0.716 to 0.929. This result showed a strong correlation between the factor (latent variable) and the analysis items (explicit variable).
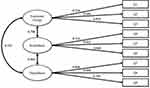 |
Figure 1 Three factors model. |
As shown in Table 2, the ratio of chi-square to degree of freedom was a little higher (CFI=0.934 > 0.9, NFI=0.928 > 0.9, NNFI=0.901 > 0.9, TLI=0.901 > 0.9, IFI=0.934 > 0.9). These indexes met the criterions, so we can draw the conclusion that the fitting index of the model was good.
 |
Table 2 The Three-Factor Model Indexes |
Convergence Validity
Confirmatory factor analysis (CFA) was conducted for three factors and nine items. As shown in Table 3, the AVE values of the three factors were all greater than 0.5, and the CR values were all higher than 0.7, which means that the scale had good convergence validity.
 |
Table 3 Model AVE and CR Indexes Results |
Discriminant Validity
As illustrated in Table 4, according to the analysis of discriminant validity, the square root of AVE square root values for the factors were 0.860, 0.867, and 0.839, which were greater than the maximum value of absolute correlation coefficient between factors (0.779), meaning that the scale had good discriminant validity.
 |
Table 4 Pearson Correlation and AVE Square Root Value |
Coefficients of Internal Consistency
As Table 5 shown, the reliability coefficient was 0.939, which indicated that the reliability quality of the research data was very high. The reliability coefficient did not increase significantly after any item was deleted, which meant that the item should not be deleted.
 |
Table 5 Cronbach α Coefficient |
Calculation of Reliability of Subscale
As shown in Table 6, the Cronbach reliability coefficients of the three subscales were all greater than 0.8, which indicated that the reliability quality of the subscale was high.
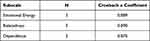 |
Table 6 Reliability Coefficient of Each Subscale of IT Identity |
Discussion
In making several revisions to the original scale, we developed an IT identity scale that is applicable to Chinese culture and achieved the overall aim of this study. After analysis, the revised scale performed well on all indicators.
We did two important things when revising the scale. Firstly, the IT identity scale developed by Carter was based on the MS Office environment, in China, WPS Office is used in many scenarios because of its convenience and comprehensive functions, so we replaced the MS Office environment with WPS Office when revising the scale. Secondly, in the original scale, there were three factors, each containing four items, and in the revision process, we combined two of the items into one for each factor because their meanings were consistent in Chinese context: in the emotional energy dimension, “energized” and “pumped up” both indicate that the individual is energetic when using the WPS Office, and in the relatedness dimension, “connected with” and “linked” both indicate that the individual is connected to the WPS Office when using it; in the dependence dimension, “dependent and reliant” both indicate that the individual is dependent on the WPS Office.
In the factor analysis, the factors loading of all items exceeded 0.7. The feasibility of adopting the same three-factor model used to assess the MS Office environment to measure IT identity in the context of WPS Office was verified. According CFA, the indexes were good. After localization, the modified model’s indexes (ie, χ2/ DF, CFI, and NNFI) are similar to those of the original model.2 We believe that the reasons for this result are as follows: (1) After translation and back translation, the sentence structure and meaning of the items in the questionnaire were revised locally, and the scale was reduced according to the repetition of the items, which aligned with the reading and analytical habits of Chinese people. (2) The attributes of WPS were similar to those of MS Office. (3) The structure of our scale was similar to Carter’s.46 The IT identity of WPS Office also assumed a three-factor structure, which verified our hypothesis. We thus determined that the same scale structure can be used to measure IT identity in the contexts of both WPS and MS Office. Moreover, due to the good indicators, there is no need to modify the item expression and questionnaire structure.
Information technology is developing rapidly and it has become one of the indispensable resources for individuals. As Cater says, IT identity has become part of an individual’s sense of self,1 and relevant researchers have identified the positive significance of IT identity for people in the areas of healthcare,22,23 consumption,24 and Education.30,31 This study was conducted in a Chinese cultural context, and the Chinese version of the IT Identity Scale performed well, providing a reliable and valid measurement tool for scholars in related field.
However, this study did face several limitations that need to be addressed. First, our sample differed from Carter’s in that our participants consisted of junior high school students, while his were mostly individuals between the ages of 20 and 49 (59%). Our group was less representative of the overall domestic cultural demographics, so we suggest that future studies expand the scope of the sample in order to make it more representative. Second, we decided to focus on the use of WPS Office instead of the use of MS Excel in order to align our approach with the Chinese cultural context, but a proportional group of people who use MS Office does exist in China. In 2020, Carter and his team examined two platforms while analyzing desktop computing: MS Excel, a pervasive and establishing technology with a relatively unchanging feature set, and mobile devices, which were more dynamic and emergent. They examined smartphones within the context of IT consumerization (ie, employees’ use of consumer technologies in the workplace for work-related purposes).57 Unlike Carter and his team, we only measured IT identity in one situation, which is an element that we need to improve in a follow-up study. We carried out item analysis, confirmatory factor analysis, and alpha coefficient analysis and proved good performance; however, if possible, we need to analyze multiple situations and clarify the stability of the scale in order to conduct further retesting of the initial sample group.
Conclusion
Based on Carter’s IT Identity Scale, we have revised the scale to obtain a Chinese version of the IT Identity Scale. After various analyses, the revised scale has good psychometric properties and can measure affective energy, relatedness, and independence dimensions related to IT identity. The Chinese version of the IT Identity Scale provides researchers with a reliable and valid tool for measuring identity in information technology.
Ethics Statement and Informed Consent
The study was approved by the Institutional Review Board (or Ethics Committee) of Ethics Committee of Shandong Normal University and this study was conducted in accordance with the Declaration of Helsinki. The parents of the participants signed an informed consent form, and the participants were told that the information they provided was anonymous and confidential. We declare that participants in our research study allow us to use their data for academic research and publication.
Author Contributions
All the authors made significant contributions to the conception and design of the paper, the acquisition of data, or the analysis and interpretation of data. Everyone participated in the drafting or revision of articles to obtain important knowledge content, agreed to submit to the current journal, gave final approval of the version to be published, and agreed to be responsible for all aspects of the work.
Funding
This work was supported in part by the projects of Shandong Natural Science under Grant ZR2020MF158, National Students Innovation and Entrepreneurship Training Program, China [grant number 202110445245X], [grant number 2021180127]. The key funding project of the 13th five-year Plan of Educational Science in Shandong Province in 2019: research on the Analysis and Application of Educational enrollment examination data [grant number BZZK201901]. The research project of undergraduate teaching reform in Shandong Province in 2020: the reform of the teaching method of “mixed bisection classroom” facing the construction point of “two Thousand Thousand Project” for first-class undergraduate majors [grant number M2020210].
Disclosure
The authors report no conflicts of interest in this work.
References
1. Carter M. IT identity: developing valid measures through CFA-based MTMM analysis.
2. Carter M. Information Technology (IT) Identity: A Conceptualization, Proposed Measures, and Research Agenda. Clemson University; 2012. Available from: https://tigerprints.clemson.edu/all_dissertations/901. Accessed March 22, 2022.
3. Hongqiang H, Zhipeng W. Study on information technology service classification and definition. Info Technol Standard. 2013;2013(4):28–31.
4. Nach H, Lejeune A. Coping with Information Technology Challenges to Identity: A Theoretical Framework. Vol. 26. Social Science Electronic Publishing; 2021:618–629.
5. Larson RW, Wilson S, Brown BB, et al. Changes in adolescents’ interpersonal experiences: are they being prepared for adult relationships in the 20th century? J Res Adolesc. 2002;12(1):31–68. doi:10.1111/1532-7795.00024
6. Carter M, Grover V. Me, my self, and I(T): conceptualizing information technology identity and its implications. Mis Quart. 2015;39(4):931–958. doi:10.25300/MISQ/2015/39.4.9
7. Burke R, Peter J. Identities and self-verification in the small group. Soc Psychol Quart. 1995;58:61–73.
8. Kokswijk JV. Granting personality to a virtual identity. Int J Human Soc Sci. 2008;2(4):207–215.
9. Shotter J. The social construction of our inner selves. J Constr Psychol. 1997;10(1):7–24. doi:10.1080/10720539708404609
10. Thoits PA, Virshup LK. Me’s and We’s: Forms and Functions of Social Identities. Oxford University Press; 1997.
11. MacKinnon NJ. Symbolic interactionism as affect control. Social Forces. 1994;75(4):1489–1490.
12. Stryker S, Burke PJ. The past, present, and future of an identity theory. Soc Psychol Quart. 2000;63(4):284. doi:10.2307/2695840
13. Tajfel H. The social identity theory of intergroup behavior. Psychol Intergroup Relations. 1986;13(3):7–24.
14. Turner ME, Pratkanis AR, Probasco P, Leve C. Threat, cohesion, and group effectiveness: testing a social identity maintenance perspective on groupthink. J Pers Soc Psychol. 1992;63(5):781.
15. Terry DJ, Hogg MA, White KM. The theory of planned behaviour: self-identity, social identity and group norms. Br J Soc Psychol. 1999;38(Pt 3):225–244. doi:10.1348/014466699164149
16. Smith-Lovin L, Heise DR. Analyzing Social Interaction: Advances in Affect Control Theory. Gordon and Breach Science Publishers; 1988.
17. Swann WB. Identity negotiation: where two roads meet. J Pers Soc Psychol. 1987;53(6):1038–1051. doi:10.1037/0022-3514.53.6.1038
18. Meyrowitz J. No Sense of Place: The Impact of Electronic Media on Social Behavior. Oxford University Press; 1985.
19. Altheide DL. An ecology of communication. Sociol Quart. 1994;35(4):665–683. doi:10.1111/j.1533-8525.1994.tb00422.x
20. Baldwin M. Dictionary of Philosophy and Psychology. Macmillan Co.; 1998.
21. Alahmad R, Carter M, Pierce C, Robert L. The impact of enterprise social media identity on job performance and job satisfaction.
22. Reychav I, Beeri R, Balapour A, et al. How reliable are self-assessments using mobile technology in healthcare? The effects of technology identity and self-efficacy. Comput Human Behav. 2018;91:52–61. doi:10.1016/j.chb.2018.09.024
23. Esmaeilzadeh P. How does IT identity affect individuals’ use behaviors associated with personal health devices (PHDs)? An empirical study - ScienceDirect. Info Manag. 2020;58(1):103313.
24. Huang TL. Psychological mechanisms of brand love and information technology identity in virtual retail environments. J Retail Consum Services. 2019;47:251–264. doi:10.1016/j.jretconser.2018.11.016
25. Cheng Z, Wang S. Review on user’s active behavior in virtual community based on role identity theory. J Beijing Univ Aeronaut Astronaut. 2017;30(02):78–81.
26. Kramer GM. Identity theory. Lambda book report. 2003.
27. Wang W, Xu J. Information Technology Identity: People’s Self-Perception in the Digital Age. Entrepreneur Scholar Program of Jinan University; 2019.
28. Kim HW, Chan HC, Kankanhalli A. What motivates people to purchase digital items on virtual community websites? The desire for online self-presentation. Info Syst Res. 2012;23(4):1232–1245. doi:10.1287/isre.1110.0411
29. Brand M, Young K, Laier C, Lfling W, Potenza MN. Integrating psychological and neurobiological considerations regarding the development and maintenance of specific Internet-use disorders: an Interaction of Person-Affect-Cognition-Execution (I-PACE) model. Neurosci Biobehav Rev. 2016;71:252–266.
30. Dincher M, Wagner V. Teaching in times of COVID-19: determinants of teachers’ educational technology use. Educ Econ. 2021;29:461–470. doi:10.1080/09645292.2021.1920000
31. Shi JH. Teachers’Role in online public English teaching for graduate students in the context of COVID-19 epidemic. J North China Univ Water Resources Electric Power. 2020;36(6):100.
32. Baccon LA, Chiarovano E, Macdougall HG. Virtual reality for teletherapy: avatars may combine the benefits of face-to-face communication with the anonymity of online text-based communication. Cyberpsychol Behav Soc Netw. 2018;22:158–165.
33. Valkenburg Patti M, Jochen P. Who visits online dating sites? Exploring some characteristics of online daters. Cyberpsychol Behav. 2007;10(6):849–852.
34. Valkenburg PM, Peter J. Adolescents’ identity experiments on the internet consequences for social competence and self-concept unity. Communic Res. 2008;35(2):208–231. doi:10.1177/0093650207313164
35. Gauntlett D, Horsley R. Web.studies. 2004.
36. Parcel TL. Differentiation between social groups: studies in the social psychology of intergroup relations. Am J Sociol. 1978;86(5):1193–1194. doi:10.1086/227378
37. Abrams D, Hogg MA. Social Identity Theory: Constructive and Critical Advances. Pearson Education Limited; 1990.
38. Zhou J, Mao Z. User identity construction in online community: a case study of Douban. Contemp Commun. 2012;2012(01):74–76.
39. McMillan SJ, Morrison M. Coming of Age with the Internet: A Qualitative Exploration of How the Internet Has Become an Integral Part of young People’s Lives. New Media & Society; 2006.
40. Moon JP, Sanders GL. The role of virtual social identity through blog use in social life.
41. Carter M, Grover V, Thatcher JB. Mobile Devices and the Self: Developing the Concept of Mobile Phone Identity. IGI Global; 2013.
42. baike.baidu.com. Douban; 2021. Available from: https://www.douban.com/.
43. Li C. Improvement of opac based on web2.0 from the experience of douban. Res Library Sci. 2010;15:16.
44. Hao LI, Wang P. The Cultural Identity in the Network Era——A Study of Tianjin Wei Group on Douban Webpage. Journal of Xinjiang University; 2015.
45. Ling R. Hyper-coordination via mobile phones in Norway. Perpetual contact mobile communication private talk public performance. 2002.
46. Carter M, Petter S, Grover V, Thatcher JB. IT identity: a measure and empirical investigation of its utility to IS research. J Assoc Info Syst. 2020;21(5):1313–1342. doi:10.17705/1jais.00638
47. Yu T, Si Y, Meng W, Bian Y, Gao F. Mediating factors of the association between shyness and generalized pathological internet use in Chinese university students. Int J Ment Health Addict. 2018;17(3):555–572.
48. Wang P, Yan Y, Gao F, Zhang R, Tian Y. The effect of shyness on adolescent network problem behavior: the role of gender and loneliness. Front Psychol. 2020;11:803.
49. Zhang S, Tian Y, Sui Y, et al.Relationships between social support, loneliness, and internet addiction in Chinese postsecondary students: a longitudinal cross-lagged analysis. Front Psychol. 2018;9:1707.
50. Wang R, Yang S, Yan Y, Tian Y, Wang P. Internet gaming disorder in early adolescents: gender and depression differences in a latent growth model. Healthcare. 2021;9:1188. doi:10.3390/healthcare9091188
51. Shuttleworth M, Cowie M. Dictionary of Translation Studies. Shanghai Foreign Language Education Press; 2004.
52. Han C. Analysis on Impact on College Computer Application Teaching by Domestic Office Software.Electronic Technology & Software Engineering. 2017;1(1).
53. CFi.CN Text of the first quarter report of Jinshan Office in 2020; 2020. Available from: http://www.zszk_quote.cfi.net.cn/.
54. Bai Y, Di M, Huo Y, Wang J, Zhao M. The structure of self-esteem: a bifactor modeling approach of the self-liking/self-competence scale-revised (slcs-r) in Chinese preadolescents. Curr Psychol. 2021;2:1–9.
55. Kato T. Examination of the coping flexibility hypothesis using the coping flexibility scale-revised. Front Psychol. 2020;11. doi:10.3389/fpsyg.2020.561731
56. Hang Z, Jiangping Z, Zhijin H. The Chinese version of the appreciation questionnaire in the relationship is revised. Chin J Clin Psychol. 2020;28(4):718–723.
57. Wenzel S. App’ification of Enterprise Software: A Multiple-Case Study of Big Data Business Applications. Springer International Publishing Springer International Publish-ing; 2014.
58. Burke RPJ. Identities and self-verification in the small group. Soc Psychol Q. 1995;58(2):61–73.
 © 2022 The Author(s). This work is published and licensed by Dove Medical Press Limited. The full terms of this license are available at https://www.dovepress.com/terms.php and incorporate the Creative Commons Attribution - Non Commercial (unported, v3.0) License.
By accessing the work you hereby accept the Terms. Non-commercial uses of the work are permitted without any further permission from Dove Medical Press Limited, provided the work is properly attributed. For permission for commercial use of this work, please see paragraphs 4.2 and 5 of our Terms.
© 2022 The Author(s). This work is published and licensed by Dove Medical Press Limited. The full terms of this license are available at https://www.dovepress.com/terms.php and incorporate the Creative Commons Attribution - Non Commercial (unported, v3.0) License.
By accessing the work you hereby accept the Terms. Non-commercial uses of the work are permitted without any further permission from Dove Medical Press Limited, provided the work is properly attributed. For permission for commercial use of this work, please see paragraphs 4.2 and 5 of our Terms.
