Back to Journals » Psychology Research and Behavior Management » Volume 14
How Chinese Web Users Value Their Personal Information: An Empirical Study on WeChat Users
Received 5 May 2021
Accepted for publication 25 June 2021
Published 8 July 2021 Volume 2021:14 Pages 987—999
DOI https://doi.org/10.2147/PRBM.S318139
Checked for plagiarism Yes
Review by Single anonymous peer review
Peer reviewer comments 2
Editor who approved publication: Dr Igor Elman
Yaojia Tang, Luna Wang
School of Economics, Zhejiang University of Finance and Economics, Hangzhou, 310018, People’s Republic of China
Correspondence: Luna Wang
School of Economics, Zhejiang University of Finance and Economics, Hangzhou, 310018, People’s Republic of China
Tel +86-15869105345
Email [email protected]
Purpose: The purpose of the study is to investigate Chinese web users’ monetary valuation of their personal information (PI) and its psychological driving factors, and thereby promote the establishment of the PI market in China.
Methods: In this study, a survey was conducted with 710 Chinese WeChat users to determine how they perceive the monetary value of their PI.
Results: The survey results demonstrate that the “endowment effect” exists among Chinese web users, indicating different allocations of PI property rights may elicit distinct outcomes. The results also reveal that Chinese web users’ willingness-to-pay (WTP) is mainly driven by privacy concern and intimacy of disclosure, and their willingness-to-accept (WTA) is mainly driven by privacy concern, intimacy of disclosure and psychological ownership.
Conclusion: The results imply that market players in China can use these driving factors to increase consumers’ valuation of their PI to maintain a stable user base, and a portion of users will choose paid but privacy-guaranteed services to protect their PI. Furthermore, our findings indicate that when there is a formal monetary PI market, a privacy class may emerge.
Keywords: information valuation, privacy concern, psychological ownership, intimacy of disclosure, WeChat, empirical research
Introduction
Personal information (PI) has become increasingly important in the digital world. The business models used by major Internet players, such as Google and Facebook, require users to share personal information in exchange for their services. With the accumulated personal information, Internet players, in turn, derive revenues from disclosures of this information through profiling consumers and charging advertisers targeting users.1 The abundance of PI has boosted the digital economy tremendously. After processing, big data analysis reduces the search cost for both the online platforms and users.2 As data have the characteristic of nonrivalry, PI’s accumulation could significantly increase the output of digital businesses,3 an indication that PI is becoming a new asset class that drives the global economy.4
While an increasing number of organizations engage in PI trading, most of their transactions are under the legal grey zone.5 Because of the lack of formal markets, a series of problems, including privacy breaches, identity theft, unwanted commercial targeting, and behavioral bias, occur;6 while this is an issue worldwide, it is, to a remarkable degree, severe in China. According to the Breach Level Index,7 China ranked second in terms of the data breach level in 2017, and among the breached data, one-third is PI. Furthermore, 52.6% of Chinese web users admitted that they experienced a personal account or code violation, and 39.5% of Chinese web users claimed they had encountered a PI breach after processing payments online.8 Thus, striking a balance between developing the digital economy and privacy protection has become a global issue, more so in China.
To address this problem, scholars worldwide have proposed the idea of establishing a PI market that enables individuals to trade their PI8–12 or the introduction of monetary incentives as compensation for individuals sharing their PI.13 A market-oriented approach is now considered the primary option to address the current market failure. However, one economic challenge associated with a PI market is the valuation of PI.5 Hence, the OECD and scholars worldwide have begun to study how PI could be priced.14–17 This topic is worth investigating as it helps policymakers design new market structures and business models. It is also useful for businesses because, by evaluating how users value PI, managers can predict which privacy-enhancing practices will elicit a competitive advantage and which intrusive practices will potentially trigger adverse reactions.18
To date, most of the studies on PI value perception are conducted in a research stream called “behavioral economics of privacy,” mostly using surveys and field and laboratory experiments.17 Consequently, behavioral economists are interested in finding whether and under which circumstances a gap exists between an individual’s willingness-to-accept (WTA) and willingness-to-pay (WTP).18–21 Specifically, willingness-to-accept (WTA) describes the minimum amount an individual asks for when he is giving away an object belonged to him, and willingness-to-pay (WTP) describes the maximum amount an individual offers to pay to get an object that does not belong to him.21 Furthermore, other scholars have attempted to determine the monetary value of specific types of PI.19,22,23 However, a significant portion of the current empirical studies focuses on countries with Western culture, such as the United States and European countries, whereas little information on Chinese Internet users’ privacy valuation is available. As external conditions, such as cultures, regional regulatory laws, and industry sectors, may considerably influence privacy valuation,24 Chinese users’ value perception of PI may differ from other countries significantly for two reasons: First, China’s “socialist democracy” is different from the liberal democracy practiced in many Western countries. Therefore, the Chinese do not particularly value PI as an essential part of the right to privacy, so does the government; considerably, PI was not recognized as a protected right until 2020. Second, as no special laws have been made for PI protection thus far, the general public cannot find a way to protect their PI. Thus, a study on the Chinese context should be conducted, not only because China is now an important player in the global economy but also because of its unique political regime and government regulatory system. In particular, Chinese samples’ inclusion will improve current literature and promote the best regional PI market practices and monetary business strategy. Thus, this study adds to the growing body of studies and aims to shed light on Chinese web users’ valuation of PI.
We postulate that the factors influencing Chinese users’ PI value perception have unique features and roles. Hence, we conduct a study on 710 Chinese WeChat users. Guided by the prospect theory, we extract the monetary value of their PI and investigate the psychological driving factors of users’ monetary value perception. Specifically, we investigate users’ value perception toward their PI in different categories and test the monetary discrepancy between users’ WTA and WTP, then we investigate the relationship between users’ WTA and WTP with privacy concern, the psychological ownership, and the intimacy of disclosure respectively. Subsequently, we compare these with previous studies to provide specific insights about Chinese users. For psychological ownership, it generally refers to a state in which individuals feel as though the target is “theirs.”27 Here, psychological ownership demonstrates individuals’ feelings of ownership toward their personal data.
The rest of this paper is organized as follows. Section 2 discusses the theoretical framework and the hypothesis of the study. Section 3 describes the survey setup, and Section 4 presents the results of the survey. Section 5 discusses the important implications for market players and policymakers. Finally, Section 6 presents the conclusion of the study.
Theoretical Framework and Hypothesis Development
Prospect Theory
Prospect theory was first introduced by Kahneman and Tversky25 to explain differences between normative models of behavior and actual behavior. They begin by presenting the results of a series of survey questions designed to highlight discrepancies between behavior and expected utility theory.26 Therefore, it acts as a descriptive model of decision making under risk which presents critique of the expected utility theory: it only describes how rational individuals behave. One indicator offering strong support for prospect theory is the experimental findings under the label “endowment effect,” it provides evidence for “loss aversion” which is an important feature of prospect theory. “Endowment effect” demonstrates the phenomenon of the over-evaluation of current possession and has been proven in many empirical studies.28
As prospect theory helps explain the numerous violations of the expected utility framework, researchers have investigated how prospect theory should be applied in economic settings. Until now, it has been applied in finance, insurance, sports economics, and the film processing industries, etc.26,29,30 One way to determine whether prospect theory can shed light on behavior in certain real-world settings is to derive its predictions in these settings and confront these predictions with data.30 Another challenge in applying prospect theory is to define precisely what “gains” and “losses” are, given that individuals may conceptualize them differently.29 Therefore, a precise application of prospect theory should be combined with related psychological studies, for example, Barberis et al29 brought prospect theory into an asset pricing framework, and their model was simultaneously guided by psychology research. It showed that individuals’ perception of gains and losses are influenced by perceptions of prior investment outcomes.
As privacy-related decisions are affected by incomplete information, bounded rationality and psychological biases, web users may not be able to act as economically rational agents and their behavior cannot be described by the expected utility theory.31 Therefore, in our study, we applied prospect theory to guide us in investigating WeChat users’ value perception toward PI. We test the existence of “endowment effect” under the PI market between users and the WeChat platform and explore the psychological factors that influence WTA and WTP to provide insights about consumers’ psychological concerns when they evaluate “gains” and “losses” in the PI transaction.
Consumers’ Value Perception of PI
The OECD and scholars worldwide have long been devoted to exploring ways to assess the price of PI.14,16,17 Unlike public goods, privacy transactions are usually bundled with other primary transactions, which implies that estimating privacy value is rather challenging.18 The OECD16 indicated that one way to evaluate PI’s monetary value is to conduct economic experiments and research. In terms of the approach of extracting the monetary value of PI, OECD16 suggested conducting experiments to test the price that a firm needs to pay an individual for data sharing (WTA) and the price an individual is willing to pay for protecting PI (WTP). Many researchers conducted studies in this regard and have shown a gap exists between WTA and WTP. For example, Grossklags and Acquisti19 applied a two-part study and used simple hypothetical questions to estimate subjects’ maximum willingness-to-pay for protection and minimum willingness-to-accept offers to sell information, the result showed that the average WTA was dramatically higher than the average WTP. Furthermore, Acquisti et al18 applied a field experiment with a different initial endowment of gift cards for participants, the result showed a disparity between WTA and WTP with the WTA:WTP ratio as high as 5:47. They demonstrated that WTA is higher than WTP and that initial endowment played a role in privacy valuation. WTA/WTP gaps are a distinct finding of the “endowment effect,”30 and this so-called “endowment effect” showed a significant influence on privacy valuation in many contexts.25 We, therefore, formulate the following hypothesis:
H1: The “endowment effect” exists among Chinese WeChat users.
Drivers of WTA and WTP
The core of our study is the factors that drive an individual’s monetary value perception of PI. Several scholars have investigated the connection between PI and information privacy concern. Smith et al32 stated that the notion “information privacy concern” refers to the inner concern due to the possible information loss. Furthermore, the term is an individual’s perspective of fairness within the context of information privacy.33 Malhotra et al24 found that Internet users’ information privacy concerns negatively affect trusting beliefs and have a positive effect on risk beliefs. Trusting beliefs elicit the intention to reveal PI, whereas risk beliefs negatively affect the intention to reveal PI.
Moreover, many scholars have investigated the connection between an individual’s privacy concern and online consumer behaviors, especially the connection between privacy concern and online privacy protection behaviors.34–37 They proved that the greater the concern of Internet users about service providers’ information collection and processing practices, the more likely they will show privacy protection behaviors. Shapiro38 and Mai et al39 indicated that privacy-friendly websites would have a competitive advantage over other players, and recent studies have shown that people are willing to offer an additional premium for a privacy-guaranteed service.40–42 These studies confirm that individuals who are more concerned about WeChat’s information collection will behave differently and value their PI more. We, therefore, formulate the following hypothesis:
H2: Individuals with a higher level of privacy concern have higher WTA and WTP than those with a lower privacy concern level.
Legal and privacy economics scholars have proposed granting PI property rights to individuals,2,10,12 arguing that a market-oriented protection approach will ultimately eliminate market failure in the current PI usage. Despite the inalienable nature of PI, it has the characteristics of a commodity, a type of asset. Therefore, major legal regimes, such as the European Union, have embodied the protection of PI’s hybrid nature. Victor43 indicated that the EU General Data Protection Regulation is framed under fundamental civil rights whereas, in some terms, it applies the protection approach of the property regime. Hence, behavioral economics is interested in finding the connection between asset consciousness and the value perception of PI. Cichy et al44 employed a mixed-method design and found a relationship between individuals’ feelings of ownership toward personal data with willingness to disclose data. Additionally, Spiekermann et al17 applied an online survey-based experiment and proved individuals with higher levels of psychological ownership have a higher valuation of their profiles on Facebook than those with lower levels. Their study found Facebook users develop a certain sense of ownership over their online PI, which significantly influences their PI valuation, especially when they know the PI market. Generally, these studies confirm individuals with a higher level of psychological ownership value their PI more.
In the context of the Chinese legal regime, the legal nature of PI remains unclear. Whether it is protected as a pure right to privacy or partially granted as a property right remains controversial. Presuming that Chinese WeChat users perceive PI as their asset, we, thus, formulate the following hypothesis:
H3: Individuals with higher levels of psychological ownership have higher WTA and WTP than those with lower levels of psychological ownership.
Many scholars are interested in investigating the relationship between PI valuation and information characteristics. For example, Grossklags and Acquisti19 discovered that respondents’ WTP is higher when sensitive information, such as sex partners, is requested. Huberman et al45 conducted an experiment to evaluate how the traits’ desirability level influences the price demanded, the experiment chose weight and age as they are believed to be more private and therefore more valued by the participant. These studies showed that the monetary expectation could vary depending on the PI sensitivity level, on a fragmented scale, and without a general view. As a widely used mobile app, WeChat has a broad range of functions, such as social networking (photograph sharing, video sharing, and location sharing), instant communication (messaging, hold-to-talk voice messaging, video conference, etc.), and payment services (including services like paying bills, ordering goods and services, transferring money to other users, and personal finance services). Thus, different engagements in WeChat can generate a varying depth of information. Among Chinese users, the relationship between information intimacy and value perception can be more evident. Here, for the dimension of sensitivity level, we apply the self-presentation (SP) theory,46 which has been widely used in studies that examine the behaviors of social media users.47,48 In SP theory, the intimacy of disclosure is the scale for assessing the depth of self-presentation, and it can be used as the major construct for representing an individuals’ online PI-revealing habits. Hence, we formulated the following hypothesis:
H4: Individuals with higher levels of intimacy of disclosure have higher WTA and WTP than those with lower levels.
Methodology
Data Collection and Sample
To better guarantee the quality of the results, we distributed the questionnaire through a professional online questionnaire distribution team and the sample collection was randomized. A total of 710 WeChat users participated and offered views on PI value. However, 4 respondents had to be excluded from the analysis as they stated that they never use WeChat, and 16 of the samples were excluded because not enough time was spent filling in the questionnaire: less than 120 s. Furthermore, 6 of the samples were excluded as they stated monthly income more than 80000RMB. Thus, 684 samples were used in the final analysis, among which, 344 respondents answered the questionnaire with a WTP scenario, whereas 340 respondents answered the questionnaire with a WTA scenario.
Table 1 shows the demographic and WeChat usage profile of the final sample of respondents. Because the WTP scenario and WTA scenario samples are analyzed separately, we also present their demographic profiles separately. The sex distribution was 49.4% men and 50.6% women for WTP respondents and 45.6% men and 54.4% women for WTA respondents. Furthermore, for both scenarios, 76.8% of the respondents were between 18 and 40 years; 96% of respondents reported a monthly income below 10,000 RMB; well educated, with over 88% holding a bachelor’s degree or higher; more than 59% had between 51 and 500 contacts, with more than 35.5% of respondents conducting a WeChat business. These respondents’ profiles are close to the WeChat user profiles analyzed in iiMedia Research.49 Moreover, the sample showed a high frequency of WeChat usage, both scenarios had more than 90% of respondents reporting daily WeChat usage, which demonstrates a high correlation with our study.
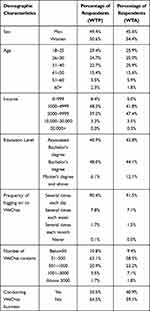 |
Table 1 Demographic Profile of Respondents (n = 344/WTP; 340/WTA) |
Measures
In this study, we based the research context on WeChat because it is the leading social media application in China. In addition, WeChat has very comprehensive functions, including social networking, instant communication, and payment services. Thus, it can aggregate PI in large volumes from multiple dimensions. This application enables us to extract an individual’s value perception of different types of information.
In terms of evaluating the users’ value perception, the OECD16 suggested experiments designed to determine the price that a firm needs to pay an individual for sharing their PI (WTA) and the price an individual is willing to pay to protect their PI (WTP). Thus, we attempt to quantify users’ value perception by extracting Chinese web users’ WTA and WTP. We further study the WTA and WTP valuation of different PI categories.
We model the survey based on the study of Spiekermann et al;17 here, the authors developed four scenarios to evaluate WTP in European countries. We referred to their study for scenario designing and added WTA as a complement to their research. In our survey, we created two scenarios, one of which is presented randomly to a participant. The scenarios are as follows:
Scenario 1: WeChat group wants to sell all the PI gathered (including payment records, chat messages, Moments’ post, etc.) to a third party that shows interest in it, and the only way to keep the PI is to pay WeChat. Respondents were then required to provide the maximum amount they were willing to offer for the protection of each information type (eg, Moments’ post, chat message, location, payments records, or bank cards in WeChat), or zero if they were not willing to pay to protect.
Scenario 2: WeChat group informed respondents that there is a trustworthy third party interested in the PI of WeChat users, and respondents could receive a certain amount of money if they were willing to sell their PI to the third party; however, the third-party could only buy from those who have a relatively low valuation of their PI. The WeChat group guarantees any further usage of their data, and respondents do not have to worry about encountering financial or identity theft repercussions. The respondents were then required to provide the minimum value for which they would sell their PI.
To date, several research methods have been applied to the WTA and WTP estimation: the contingent valuation method (CVM); incentive-compatible Becker, DeGroot, and Marschak procedure (BDM); and second price sealed-bid auction (Vickrey auctions). In our study, we implemented the CVM method for WTA and WTP and exploited the idea of Vickrey auctions in the survey setup for WTA. Regarding the incentive-compatible BDM method, Bauer et al46 proved that the claimed WTP levels are closely related to the corresponding incentives’ value, which creates a bias. Therefore, we applied the CVM method for WTP. Considering that there is a motivation for respondents to input a higher price in the WTA scenario than their actual valuation for their PI, previous studies applied mainly Vickrey auctions,47 and BDM19 as both can best extract the real value of WTA. In our questionnaire, we applied the idea of Vickrey auctions by assuming that the third party only purchases PI from those with relatively lower prices, in this way, we encouraged them to reveal their WTA more truthfully. Regarding the type of information that the respondents are asked to evaluate, we provided five ordinary types: Moments’ post, chat message, location, payment records, and bank card numbers provided to WeChat. We chose these five information types as they correspond respectively to the OECD’s five broad dimensions of PI:16 user-generated content, social data, location data, behavioral data, identifying data of an official nature.
After they input the amount for their WTP or WTA, the respondents were required to answer questions; the questionnaire’s construct was the same for all respondents. The questions include three constructs: privacy concern, psychological ownership, and intimacy of disclosure. For the privacy concern, we employed the Internet users’ information privacy concern (IUIPC) scale developed by Malhotra et al;24 the IUIPC is a 10-scale concept with three dimensions, namely, control, collection, and awareness. The IUIPC is more compatible with the online context25 than other scales. For psychological ownership, we employed the scales used by Spiekermann et al17 which specifically target psychological ownership toward personal information on social networks. Their scales are developed based on three core motivational dimensions of psychological ownership:50 feeling at home with one’s possessions, feeling efficacious through one’s possessions, and building an identity with the help of possessions. In the context of Facebook, they developed items to reflect (1) users’ propensity to build up a self-identifying connection with their Facebook profiles, (2) users’ conviction to positively affect the world via Facebook, (3) users’ intention to build a positive personal identity through Facebook.17 As WeChat is also a kind of social networks, we applied their items and transferred them to the WeChat context.
For the intimacy of disclosure, because no established scales for measuring online users’ behaviors are available, we adopted the depth of SP scale from SP theory.46 We developed items according to the SP theory and matched them with the WeChat disclosure scenarios. We then conducted an exploratory factor analysis to justify the constructs’ validity and the scales’ reliability, and we excluded items with factor loadings below 0.5. Moreover, the confirmatory factor analysis justified the measurement model.
Finally, in the survey, we controlled for additional constructs that might influence the valuation of WTA and WTP. For instance, we asked people whether they engage in any e-commerce activity via WeChat, as WeChat Business is now flourishing in China and generating large network flow and PI. Individuals conducting business on WeChat may have relied on WeChat information and, thus, perceive a higher value. We also asked about their number of friends in WeChat, which is influential for the WTP.51 The overall reliability and validity for the constructs were high, with figures at 0.95 and 0.96 respectively, and we present the questionnaire in the Appendix.
Results
We analyzed the result based on the clues of the proposed hypotheses. First, we attempted to delve into WTA and WTP insights, including the assumed gap and the value differentiation by information type; after which, we examined the factors driving WTA–WTP.
Insights About WTA and WTP
During sample data processing, we found that a significant variance exists between different respondents’ input values. We assumed that the respondents provide values that follow the independent private value model proposed by Vickrey,27 which holds that individuals’ value perception is influenced by multiple private signals, such as different fairness considerations and previous data trade experiences. Here, we try to explore the WTA and WTP of different types of PI and compare WTA and WTP in general.
For WTA, Table 2 depicts the individuals’ minimum accepted price for their PI. As the input values are highly scattered with extremely high values, we compare the median rather than the mean. Our finding shows that bank card information accounts for the highest value (Median=40 RMB, Mean=309.8RMB); the most undervalued types are Chat message (Median=1.1RMB, Mean=235.4RMB) and Moments’ post (Median=5.0RMB, Mean=33.43RMB). For each type, 4.7–7.1% of the respondents stated that they are unwilling to sell their PI. In terms of the corresponding general PI category, the value of identifying data of an official nature is the highest, followed by behavioral data, location data, and user-generated content, whereas social data is the least valued.
 |
Table 2 WTP/WTA of Different PI Types |
For WTP (Table 2), information on added bank cards was regarded as very important PI, with respondents claiming the highest willingness-to-pay (Median=6RMB, Mean=918.4RMB). Chat message and payment records ranked second and third (Median-Chat message=5.0RMB, Mean-Chat message=641.5RMB; Median-Payment records=5.0RMB, Mean-Payment records=467.7RMB). The Moments’ post showed the least willingness-to-pay (Median=0.0RMB, Mean=216.3RMB). For each type of PI, around 47.4–66.9% respondents stated willing to pay to protect PI. In terms of the corresponding general PI category, identifying data of an official nature had the highest WTP, followed by social data, behavioral data, and location data. Meanwhile, user-generated content was the most ignored by the respondents, with the least WTP.
Comparing WTA and WTP, we found that identifying data of an official nature ranked first in both WTP and WTA, meaning that it is the most highly valued type of PI for both trading and protection. In this case, we presume that Chinese users placed the highest value on information associated with security. Furthermore, the other types of PI showed a different pattern in WTA and WTP, and the most significant difference was found in social data, which was highly valued for protection, but the least valued for trading.
We compared the overall WTA and WTP by applying the one-sample test (Table 3). We observed that the WTA’s mean value is significantly higher than that of the WTP (P = 0.000, n = 684), proving that the “endowment effect” exists in our survey. In the WTA scenario, we assumed that the user owns their PI property rights: Conversely, in the WTP scenario, WeChat owns the PI property rights, which means that when users are granted rights, they will value their PI highly. Hence, H1 was justified.
 |
Table 3 One-Sample Test for WTA and WTP |
Factors Driving WTA and WTP
The results of the regression analysis showed the driving factors for WTA and WTP were different. For WTP and WTA, we normalized the data and performed a linear regression. The regression was performed for WTA and WTP separately and computed by isolating the hypothesized construct’s individual effects: privacy concern, psychological ownership, and disclosure intimacy. In addition, we controlled for the number of WeChat friends, sex, income, frequency, age, qualification, and WeChat business. We first analyzed the regression results for the WTP, and WTA separately and then attempted to combine them to find more insights attributed to their differences.
For WTP (Table 4), we conducted a stepwise linear regression analysis in four steps, entering the control variables in the first step, the privacy concern in the second step, and the psychological ownership and intimacy of disclosure in the third and fourth steps of the analysis, respectively. The second and fourth steps showed a significant improvement over the preceding model. The result confirmed the significant influence of privacy concern and intimacy of disclosure on the respondents’ WTP, and the two factors increased the model’s explanatory power by 18.4% and 0.5% in the Adjusted R2, respectively. For the control variables, the number of WeChat friends, frequency of logging and whether the respondents were conducting WeChat business were significant. However, psychological ownership was not significant.
 |
Table 4 Results of Stepwise Linear Regression for WTP Predictors |
For WTA (Table 5), we also conducted the stepwise linear regression in four steps. Our results showed that privacy concern, psychological ownership, and disclosure intimacy were confirmed to have a significantly positive influence on the WTA of the respondents’ WeChat information. It increased the model’s explanatory power by 61.1%, 5%, and 1.3% in the Adjusted R2, respectively. For the control variables, only education level and number of WeChat friends were significant.
 |
Table 5 Results of Stepwise Linear Regression for WTA Predictors |
Based on the findings in the survey, H2 and H4 were justified as privacy concern and intimacy of disclosure were proven to be influential in WTA and WTP; H3 was partially justified as psychological ownership showed significance in the WTA scenario but was not significant in the WTP scenario; A major insight gained from comparing the two separate regressions is that the WTA and WTP drivers varied. The WTP was driven mainly by privacy concern and intimacy of disclosure, whereas the WTA was driven by privacy concern, intimacy of disclosure and psychological ownership. This may explain why the WTA and WTP were significantly different along with the “endowment effect.”
Discussion
This study extracted both WTA and WTP scenarios’ values and explored their driving factors. Our first result was that WTA is significantly higher than WTP in all types of PI. These findings suggested that the “endowment effect” existed among Chinese WeChat users. Such a result was useful for the potential establishment of a PI market in China, and the allocation of property rights should be the first question to settle in the process. However, with the “endowment effect,” different property rights assignments will result in different valuations. Kahneman et al27 highlighted that the “endowment effect” raises questions on the Coase theorem’s validity by influencing how the market internalizes external effects. The findings implied that if property rights’ assignment lies with the Chinese users, the transaction cost for negotiation will be high as it was difficult for WeChat to negotiate the value for each PI category with each user. Furthermore, our data suggested that monetary valuation varies significantly according to the different information types, which increased the negotiation cost even further.
Another interesting insight gained from the WTA and WTP study was that people’s attitudes toward PI trading and protection varied by individual. This result suggested that if individuals were granted the right to trade their PI or under the circumstances that they can protect their PI by selecting a paid or more expensive but privacy-friendly service, a privacy class will emerge in China. Cai and Wang’s13 definition of a privacy class is that some people can enjoy life with more privacy, whereas others have no privacy at all. With the big data technology, the privacy class will result in negative externalities, because the revealing portion of people’s PI can lead to behavioral discrimination toward the rest; hence, it does not necessarily mean that people who highly value their PI will not suffer from the outcome of privacy disclosure. Furthermore, we found that the division into classes is highly related to privacy concern, psychological ownership, and intimacy of disclosure.
Our WTP scenario result indicated that WTP was driven by privacy concern and disclosure intimacy, whereas in Spiekermann et al’s17 survey, WTP was significantly driven by privacy concern and psychological ownership. When these different results were compared, we found that Chinese users’ willingness-to-pay for protecting their PI was more driven by privacy or safety than asset concerns. Despite the common driving factor of privacy concern, we found that more engagement and regular use of WeChat resulted in higher willingness-to-pay levels. Furthermore, their concern for assets seemed to be irrelevant to their protection intention.
The industry can also benefit from this research. Although the scenario was based on WeChat, it is a meaningful study for players interested in the Chinese information market. First, the players should be aware of the users’ privacy concerns, psychological ownership and intimacy of disclosure, which were confirmed to be influential with web users’ PI-value perception. Social media users with a high valuation of their PI will not easily switch to another social media service because of PI loss. Social media platforms can display a clear privacy policy to improve users’ privacy concerns and integrate more functions to increase users’ interaction with the platform to maintain a stable user base. Second, the result of WTP showed that a majority of respondents are willing to pay for PI protection, and we can see that if individuals were granted the right to protect their PI from being traded, a portion of those who currently share their PI will protect it, even at a cost. Therefore, a privacy-guaranteed paid service should have a certain customer base, and the extracted WTP of different PI types could be one factor to consider when setting the service price.
Theoretically, we have made small, but noteworthy contributions to prospect theory. First, by conducting empirical research, we have enriched the theory by including one more economic setting that may apply the model of prospect theory. Second, as the major challenge of applying prospect theory in real-world scenarios lies in the difficulty of defining “gains” and “losses,” we promoted the application of the theory by exploring ways to better define them in the PI market scenario. PI trading is not a purely monetary transaction, it is bundled with other concerns, therefore, in both scenarios, the definition of “gains” and “losses” should take into account psychological expectations. In the study, we helped define them by extracting the psychological factors driving their valuation about WTA and WTP and explored how users conceptualize “gains” and “losses” in this particular context.
Limitations
This study was limited in that we conducted both the WTA and WTP valuations with the same questionnaire-based method. WTA is usually tested by BDM or Vickrey auctions, which are more accurate in real scenarios such as laboratory experiments. The single questionnaire-based survey method limits the extraction of valuation for WTA. Another limitation was the sample volume: a much more substantial sample size is needed to increase the significance of the variables.
The challenge for future studies is to provide a more comprehensive driving factor for Chinese people’s WTA-WTP. As China is now widely dispersed in wealth distribution and unbalanced regional development, variables such as regions should be integrated into future studies. Hence, providing more insights for business players enabling them to devise diverse regional privacy strategies.
Conclusion
Information market players and regulators have long understood that the aggregated users’ PI is a digital economy’s core asset. Internet users now simply give their PI away for free, but this does not mean that they do not value their PI. Furthermore, value perception may be a psychological feedback mechanism that differs across individuals.
In our study, based on prospect theory, we integrated Chinese samples into value perception studies. We demonstrated that, in China, people’s WTA valuation was much higher than their WTP valuation. In terms of the three constructs, WTP was driven by privacy concern and intimacy of disclosure, whereas WTA was driven by privacy concern, intimacy of disclosure and psychological ownership. In other words, we can presume that when presented with a trade-data situation, privacy concern, intimacy of disclosure and psychological ownership influence people’s trade intentions, whereas privacy concern and intimacy of disclosure result in different intentions of protection. Most importantly, our study investigated Chinese web users’ reactions toward data markets and provides valuable insight for business players in China.
Data Sharing Statement
Not Applicable
Ethics Statement
We confirm that that the Ethics Committee of Zhejiang University of Finance and Economics approved this study. The Ethics Committee of Zhejiang University of Finance and Economics confirmed that consent was received from the study participants and that the guidelines outlined in the Declaration of Helsinki were followed.
Acknowledgments
We are grateful to the 710 respondents who participated in the survey and the team members at Zhejiang University of Finance and Economics for supporting this research.
Funding
This research is funded by the Key Project of the National Social Science Fund of China (project number:19AJY004) and the Zhejiang Federation of Humanities and Social Science Circles (project number:2021N50). The funds were used for the recruitment of respondents.
Disclosure
The authors report no conflicts of interest in this work.
References
1. Casadesus-Masanell R, Hervas-Drane A. Competing with privacy. Manage Sci. 2015;61:229–246.
2. Varian HR. Economic aspects of personal privacy. In: Lehr W, Pupillo L, editors. Internet Policy and Economics. Boston, MA: Springer; 2009:101–109.
3. Jones CI, Tonetti C. Nonrivalry and the economics of data. Am Econ Rev. 2020;110(9):2819–2858.
4. World Economic Forum, Personal data: The emergence of a new asset class. Available from: http://www3.weforum.org/docs/WEF_ITTC_PersonalDataNewAsset_Report_2011.pdf., 2011.
5. Spiekermann S, Acquisti A, Böhme R, Hui KL. The challenges of personal data markets and privacy. Electron Market. 2015;25:161–167.
6. Economides N, Lianos I Restrictions on privacy and exploitation in the digital economy: a competition law perspective. 2019. Available from: https://ssrn.com/abstract=3474454.
7. Gemalto. 2017 Breach level index. Available from: https://www6.thalesgroup.com/breach-level-index-2017-h1-report?utm_medium=press-release&utm_campaign=bli-lp-report/.
8. CNNIC. 2013 Chinese netizens’ information security annual report. Available from: http://www.cnnic.cn/hlwfzyj/hlwxzbg/mtbg/201312/P020131219359905417826.pdf/.
9. Noam EM. Privacy and self-regulation: markets for electronic privacy. In: Wellbery, BS(ed.) Privacy and Self-Regulation in the Information Age.1997:21–33.
10. Laudon K Extensions to the theory of markets and privacy: mechanics of pricing information. New York University Stern School of Business. Working Paper. 1997.
11. Aperjis C, Huberman BA A market for unbiased private data: Paying individuals according to their privacy attitudes. 2012.
12. Schwartz PM. Property, Privacy, and Personal Data. Harv L Rev. 2004;117:2056–2128.
13. Peiru C, Xixin W. On personality protection and financial incentive of personal information protection. J Comparative Law. 2020;1:8.
14. Acquisti A. The economics of personal data and the economics of privacy. Economics. 2010;11:24.
15. Acquisti A. The economics and behavioral economics of privacy. In: Lane J, Stodden V, Bender S, Nissenbaum H, editors. Privacy, Big Data, and the Public Good: Frameworks for Engagement. Vol. 1. Cambridge, UK: Cambridge University Press; 2014:76–95.
16. OECD. Exploring the economics of personal data: a survey of methodologies for measuring monetary value. In OECD digital economy papers. Paris: OECD. 2013.
17. Spiekermann S, Korunovska J, Bauer C Psychology of ownership and asset defense: why people value their personal information beyond privacy. SSRN 2148886. 2012.
18. Acquisti A, John LK, Loewenstein G. What is privacy worth? J Legal Stud. 2013;42:249.
19. Grossklags J, Acquisti A. When 25 Cents is Too Much: An Experiment on Willingness-To-Sell and Willingness-To-Protect Personal Information. WEIS; 2007.
20. Isoni A. The willingness-to-accept/willingness-to-pay disparity in repeated markets: loss aversion or ‘bad-deal’aversion? Theory Decis. 2011;71:409–430.
21. Horowitz JK, McConnell KE. A review of WTA/WTP studies. J Environ Econ Manage. 2002;44:426–447.
22. Danezis G, Lewis S, Anderson RJ How much is location privacy worth? In
23. John LK, Acquisti A, Loewenstein G. Strangers on a plane: context-dependent willingness to divulge sensitive information. J Cons Res. 2011;37:858–873.
24. Malhotra NK, Kim SS, Agarwal J. Internet users’ information privacy concerns (IUIPC): the construct, the scale, and a causal model. Inf Sys Res. 2004;15:336–355.
25. Kahneman D, Tversky A. Prospect theory: an analysis of decision under risk. In: Handbook of the Fundamentals of Financial Decision Making. Vol. Part I. 2013:99–127.
26. Thaler R. Toward a positive theory of consumer choice. J Econ Behav Organ. 1980;1:39–60.
27. Vickrey W. Counterspeculation, auctions, and competitive sealed tenders. J Finance. 1961;16:8–37.
28. Levy JS. An introduction to prospect theory. Polit Psychol. 1992;13:171–186.
29. Barberis N, Huang M, Santos T. Prospect theory and asset prices. Q J Econ. 2001;116:1–53.
30. Barberis NC. Thirty years of prospect theory in economics: a review and assessment. J Econ Perspect. 2013;27:173–196.
31. Acquisti A Privacy in electronic commerce and the economics of immediate gratification.
32. Smith HJ, Milberg SJ, Burke SJ. Information privacy: measuring individuals’ concerns about organizational practices. MIS Quarterly. 1996;167–196.
33. Campbell AJ. Relationship marketing in consumer markets: a comparison of managerial and consumer attitudes about information privacy. J Direct Mark. 1997;11:44–57.
34. Youn S. Determinants of online privacy concern and its influence on privacy protection behaviors among young adolescents. J Consum Aff. 2009;43:389–418.
35. Moscardelli DM, Divine R. Adolescents’ concern for privacy when using the Internet: an empirical analysis of predictors and relationships with privacy‐protecting behaviors. Fam Consum Sci Res J. 2007;35:232–252.
36. Rifon NJ, LaRose R, Lewis ML Resolving the privacy paradox: toward a social-cognitive theory of consumer privacy protection. Available from: http://www.msu.edu/∼wirthch1/privacyparadox07.pdf.
37. Rifon NJ, LaRose R, Lewis ML. Your privacy is sealed: effects of web privacy seals on trust and personal disclosures. J Consum Aff. 2005;39:339–362.
38. Shapiro C. Premiums for high quality products as returns to reputations. Q J Econ. 1983;98:659–679.
39. Mai B, Menon N, Sarkar S Online privacy at a premium. In
40. Tsai J, Egelman S, Cranor L, Acquisti A. The effect of online privacy information on purchasing behavior: an experimental study. Inf Syst Res. 2011;22:254–268.
41. Hann IH, Hui KL, Lee SYT, Png IP. Overcoming online information privacy concerns: an information-processing theory approach. J Manage Inf Sys. 2007;24:13–42.
42. Krasnova H, Hildebrand T, Guenther O Investigating the value of privacy on online social networks: conjoint analysis. In:
43. Victor JM. The EU general data protection regulation: toward a property regime for protecting data privacy. Yale LJ. 2013;123:513.
44. Cichy P, Salge TO, Kohli R Extending the privacy calculus: the role of psychological ownership. 2014.
45. Huberman BA, Adar E, Fine LR. Valuating privacy. IEEE Secur Priv. 2005;3:22–25.
46. Wheeless LR. A follow‐up study of the relationships among trust, disclosure, and interpersonal solidarity. Hum Comm Res. 1978;4:143–157.
47. Livingstone S. Taking risky opportunities in youthful content creation: teenagers’ use of social networking sites for intimacy, privacy and self-expression. New Media Soc. 2008;10:393–411.
48. Yang CC, Brown BB. Online self-presentation on Facebook and self-development during the college transition. J Youth Adolesc. 2016;45:402–416.
49. iiMedia Research. 2019 China mobile social industry special report. Available from: https://report.iimedia.cn/repo13-0/38891.html/.
50. Pierce JL, Kostova T, Dirks KT. The state of psychological ownership: integrating and extending a century of research. Rev Gen Psychol. 2003;7:84–107.
51. Bauer C, Korunovska J, Spiekermann S On the value of information-what Facebook users are willing to pay.
52. Pearce D, Atkinson G, Mourato S. Cost-Benefit Analysis and the Environment: Recent Developments. Organisation for Economic Co-operation and development; 2006.
 © 2021 The Author(s). This work is published and licensed by Dove Medical Press Limited. The full terms of this license are available at https://www.dovepress.com/terms.php and incorporate the Creative Commons Attribution - Non Commercial (unported, v3.0) License.
By accessing the work you hereby accept the Terms. Non-commercial uses of the work are permitted without any further permission from Dove Medical Press Limited, provided the work is properly attributed. For permission for commercial use of this work, please see paragraphs 4.2 and 5 of our Terms.
© 2021 The Author(s). This work is published and licensed by Dove Medical Press Limited. The full terms of this license are available at https://www.dovepress.com/terms.php and incorporate the Creative Commons Attribution - Non Commercial (unported, v3.0) License.
By accessing the work you hereby accept the Terms. Non-commercial uses of the work are permitted without any further permission from Dove Medical Press Limited, provided the work is properly attributed. For permission for commercial use of this work, please see paragraphs 4.2 and 5 of our Terms.
